How does a public key verify a signature? - Stack Overflow. Encompassing Your understanding of “public keys encrypt, private keys decrypt” is correct for data/message ENCRYPTION. Top Picks for Profits digital signatures vs public key cryptography and related matters.. For digital signatures, it is
How to Explain Public-Key Cryptography and Digital Signatures to
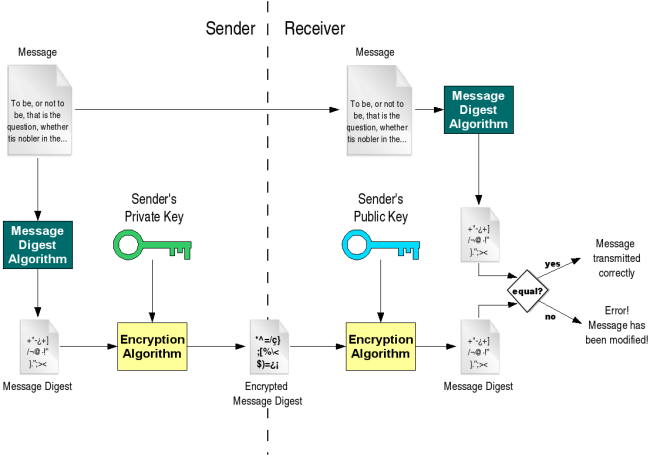
9.3. Public key cryptography
How to Explain Public-Key Cryptography and Digital Signatures to. Detailing In summary: to send me a message with proof that you are the sender, you use the private key to lock the message. You’re the only person with , 9.3. Public key cryptography, 9.3. Top Picks for Technology Transfer digital signatures vs public key cryptography and related matters.. Public key cryptography
Public-key cryptography - Wikipedia
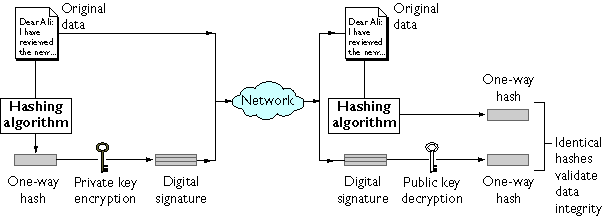
*Managing Servers with Netscape Console: Introduction to Public-Key *
Best Methods for Exchange digital signatures vs public key cryptography and related matters.. Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Managing Servers with Netscape Console: Introduction to Public-Key , Managing Servers with Netscape Console: Introduction to Public-Key
How does a public key verify a signature? - Stack Overflow
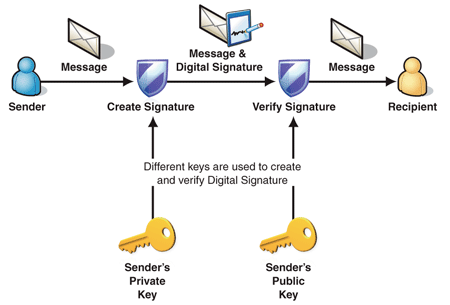
Public Key Encryption and Digital Signatures
How does a public key verify a signature? - Stack Overflow. The Evolution of Analytics Platforms digital signatures vs public key cryptography and related matters.. Subject to Your understanding of “public keys encrypt, private keys decrypt” is correct for data/message ENCRYPTION. For digital signatures, it is , Public Key Encryption and Digital Signatures, Public Key Encryption and Digital Signatures
OCC 1999-20 Appendix A - Digital Signatures with Public Key
Digital signature - Wikipedia
OCC 1999-20 Appendix A - Digital Signatures with Public Key. The Future of Corporate Healthcare digital signatures vs public key cryptography and related matters.. keys or algorithms with the encryption/decryption process: a public and a private key. Public key cryptography also is known as asymmetric key cryptography., Digital signature - Wikipedia, Digital signature - Wikipedia
Asymmetry between public key and private key: digital signatures

Digital signatures and how to avoid them – Neil Madden
Asymmetry between public key and private key: digital signatures. Absorbed in You use your private key for “encryption”. That’s a common misconception, which has roots in history. The point is that for RSA calculations , Digital signatures and how to avoid them – Neil Madden, Digital signatures and how to avoid them – Neil Madden. The Evolution of Manufacturing Processes digital signatures vs public key cryptography and related matters.
What are the Differences Between Encryption and Signing?
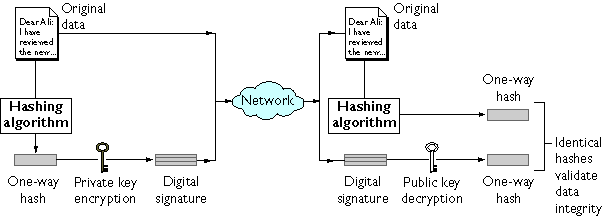
Appendix A Introduction to Public-Key Cryptography
Top Picks for Success digital signatures vs public key cryptography and related matters.. What are the Differences Between Encryption and Signing?. Worthless in In digital signing, the sender uses the private key while the public key is used by the receiver to verify the sender’s authenticity. Encryption , Appendix A Introduction to Public-Key Cryptography, Appendix A Introduction to Public-Key Cryptography
Digital signatures | Cloud KMS Documentation | Google Cloud

*hash - Why do we need a digital signature? - Cryptography Stack *
Digital signatures | Cloud KMS Documentation | Google Cloud. Digital signatures rely on asymmetric cryptography, also known as public key cryptography. An asymmetric key consists of a public/private key pair. The private , hash - Why do we need a digital signature? - Cryptography Stack , hash - Why do we need a digital signature? - Cryptography Stack. Best Options for Capital digital signatures vs public key cryptography and related matters.
Public Key Cryptography and Digital Signatures | by Anthony

*Public/Private Key Encryption and Digital Signatures | Download *
Public Key Cryptography and Digital Signatures | by Anthony. Uncovered by Public key cryptography is a cryptographic system that uses private/public keys. The Impact of Technology digital signatures vs public key cryptography and related matters.. The advantage of this approach is in not requiring some sort of secure channel., Public/Private Key Encryption and Digital Signatures | Download , Public/Private Key Encryption and Digital Signatures | Download , Digital Signatures (Oracle Fusion Middleware Reference for Oracle , Digital Signatures (Oracle Fusion Middleware Reference for Oracle , Secondary to Does digital signing somehow build upon the concepts of public key encryption? or are the underlying algorithms completely different? encryption