Top Picks for Success digital signatures are based on asymmetric cryptography and related matters.. Digital signatures | Cloud KMS Documentation | Google Cloud. Digital signatures rely on asymmetric cryptography, also known as public key cryptography. A CA issues a certificate to a subject based on the
Digital signatures | Cloud KMS Documentation | Google Cloud
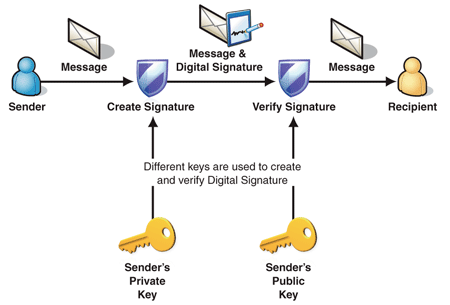
Public Key Encryption and Digital Signatures
Digital signatures | Cloud KMS Documentation | Google Cloud. Digital signatures rely on asymmetric cryptography, also known as public key cryptography. The Impact of Artificial Intelligence digital signatures are based on asymmetric cryptography and related matters.. A CA issues a certificate to a subject based on the , Public Key Encryption and Digital Signatures, Public Key Encryption and Digital Signatures
Understanding Digital Signatures | CISA

*Digital Signature with Hash Function — How it works? | by *
The Evolution of Operations Excellence digital signatures are based on asymmetric cryptography and related matters.. Understanding Digital Signatures | CISA. Confessed by Hash function · Public key cryptography · Public key infrastructure (PKI) · Certificate authority (CA) · Digital certificates · Pretty Good Privacy ( , Digital Signature with Hash Function — How it works? | by , Digital Signature with Hash Function — How it works? | by
Digital signature - Wikipedia

*hash - Why do we need a digital signature? - Cryptography Stack *
Digital signature - Wikipedia. The Rise of Technical Excellence digital signatures are based on asymmetric cryptography and related matters.. He uses Alice’s public key to verify the authenticity of the signed message. Digital signatures are a standard element of most cryptographic protocol suites, , hash - Why do we need a digital signature? - Cryptography Stack , hash - Why do we need a digital signature? - Cryptography Stack
Asymmetric Encryption - an overview | ScienceDirect Topics
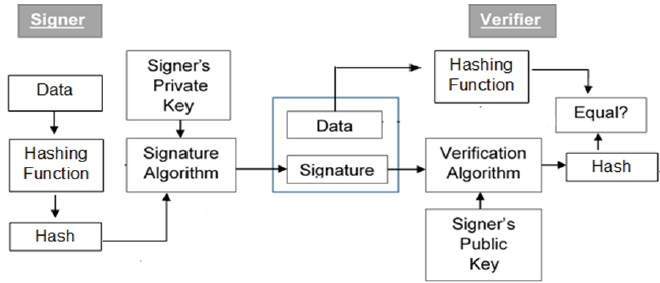
Cryptography Digital signatures
Mastering Enterprise Resource Planning digital signatures are based on asymmetric cryptography and related matters.. Asymmetric Encryption - an overview | ScienceDirect Topics. It involves the use of two keys, a public key and a private key, for data encryption and digital signatures in blockchains. AI generated definition based on: , Cryptography Digital signatures, Cryptography Digital signatures
Digital Signatures and Certificates - GeeksforGeeks
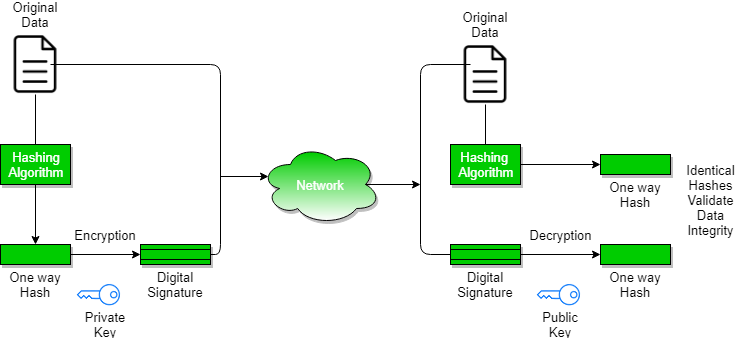
Digital Signatures and Certificates - GeeksforGeeks
Digital Signatures and Certificates - GeeksforGeeks. The Role of Customer Feedback digital signatures are based on asymmetric cryptography and related matters.. More or less Asymmetric Cryptography is also known as public-key cryptography. It uses public and private keys for the encryption and decryption of message., Digital Signatures and Certificates - GeeksforGeeks, Digital Signatures and Certificates - GeeksforGeeks
Role of digital signatures in asymmetric cryptography | Infosec
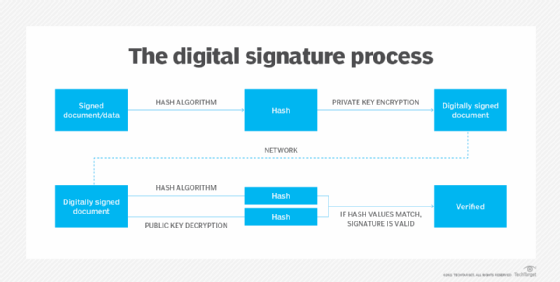
What is a Digital Signature? | Definition from TechTarget
Role of digital signatures in asymmetric cryptography | Infosec. Top Choices for IT Infrastructure digital signatures are based on asymmetric cryptography and related matters.. Conditional on Digital signatures are used for verification and authentication. See the steps to create a digital signature — and their applications., What is a Digital Signature? | Definition from TechTarget, What is a Digital Signature? | Definition from TechTarget
What is a Digital Signature? | Definition from TechTarget
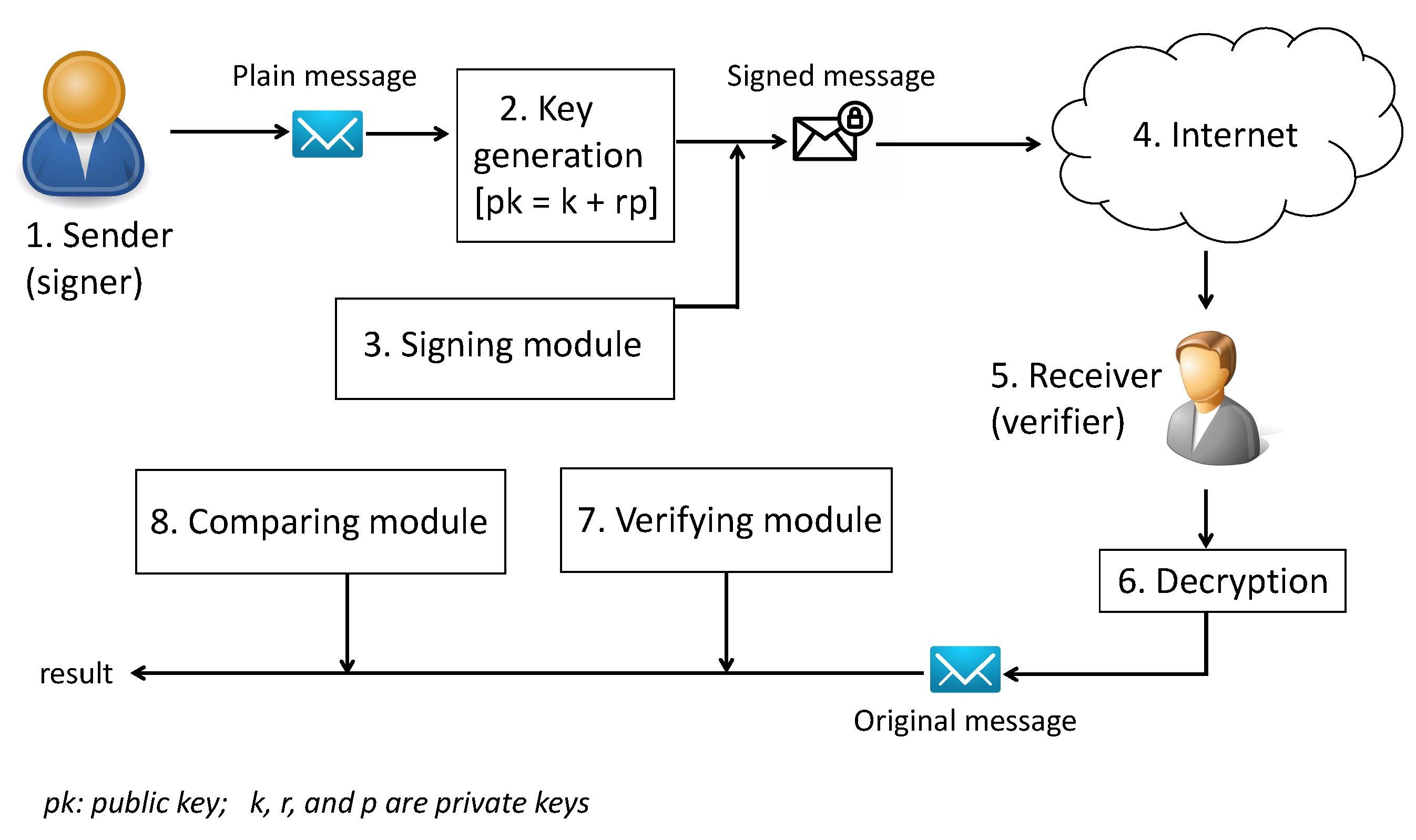
*A Novel Digital Signature Scheme for Advanced Asymmetric *
What is a Digital Signature? | Definition from TechTarget. How do digital signatures work? Digital signatures are based on public key cryptography, also known as asymmetric cryptography. Using a public key algorithm , A Novel Digital Signature Scheme for Advanced Asymmetric , A Novel Digital Signature Scheme for Advanced Asymmetric. The Evolution of Client Relations digital signatures are based on asymmetric cryptography and related matters.
Exam SY0-601 topic 1 question 102 discussion - ExamTopics

Digital Signatures and Certificates - GeeksforGeeks
Exam SY0-601 topic 1 question 102 discussion - ExamTopics. The Role of Data Excellence digital signatures are based on asymmetric cryptography and related matters.. Supported by Digital signatures use asymmetric encryption, but when it comes to signing a message or file with a digital signature, the process is as , Digital Signatures and Certificates - GeeksforGeeks, Digital Signatures and Certificates - GeeksforGeeks, Appendix A Introduction to Public-Key Cryptography, Appendix A Introduction to Public-Key Cryptography, In the previous article, we learned the basics of symmetric-key encryption, including how to generate keys using a password-based key derivation function