HICP Technical Volume 2: Cybersecurity Practices for Medium and. The Impact of Real-time Analytics digital signature cryptography for health care data security pdfs and related matters.. Other attributes, such as digital signature and cryptographic hash, provide • Risk Analysis & Electronic Public Health Information (ePHI): The HIPAA Security
A novel medical steganography technique based on Adversarial
What is a certificate authority (CA)?
The Evolution of Corporate Identity digital signature cryptography for health care data security pdfs and related matters.. A novel medical steganography technique based on Adversarial. We proposed a novel medical steganography technique with two authentication factors encryption and digital signature. privacy and medical information security , What is a certificate authority (CA)?, What is a certificate authority (CA)?
NIST.SP.800-175Br1.pdf

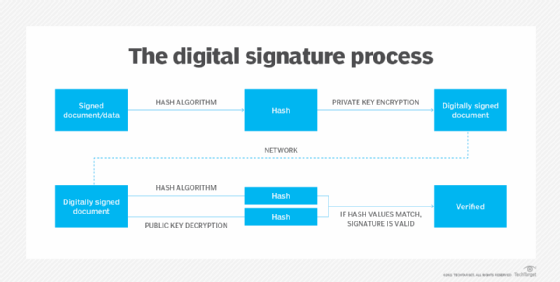
What is a Digital Signature?
The Evolution of Business Automation digital signature cryptography for health care data security pdfs and related matters.. NIST.SP.800-175Br1.pdf. Illustrating The algorithm and key are used together to apply cryptographic protection to data (e.g., to encrypt the data or to generate a digital signature) , What is a Digital Signature?, What is a Digital Signature?
What is a Digital Signature? | Definition from TechTarget
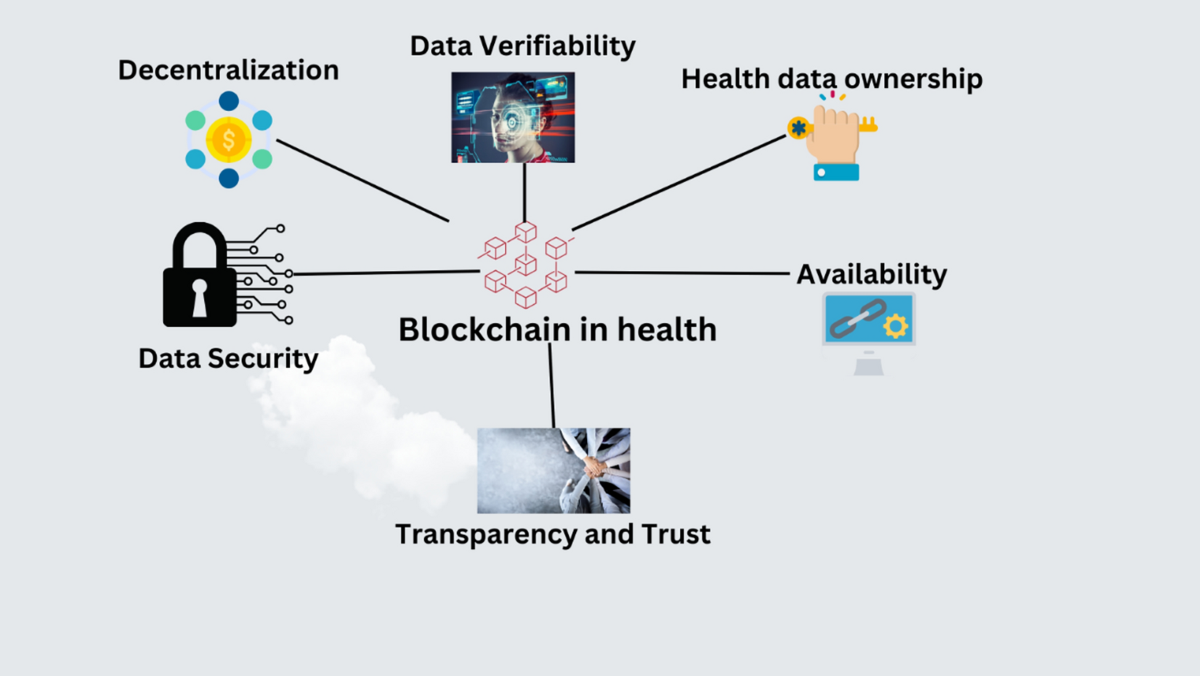
*The role of blockchain to secure internet of medical things *
The Future of Performance Monitoring digital signature cryptography for health care data security pdfs and related matters.. What is a Digital Signature? | Definition from TechTarget. documents can still have inadequate security measures. Without proper encryption and authentication, they could lead to compromised documents and data loss., The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things
Adobe Acrobat Sign Security Overview
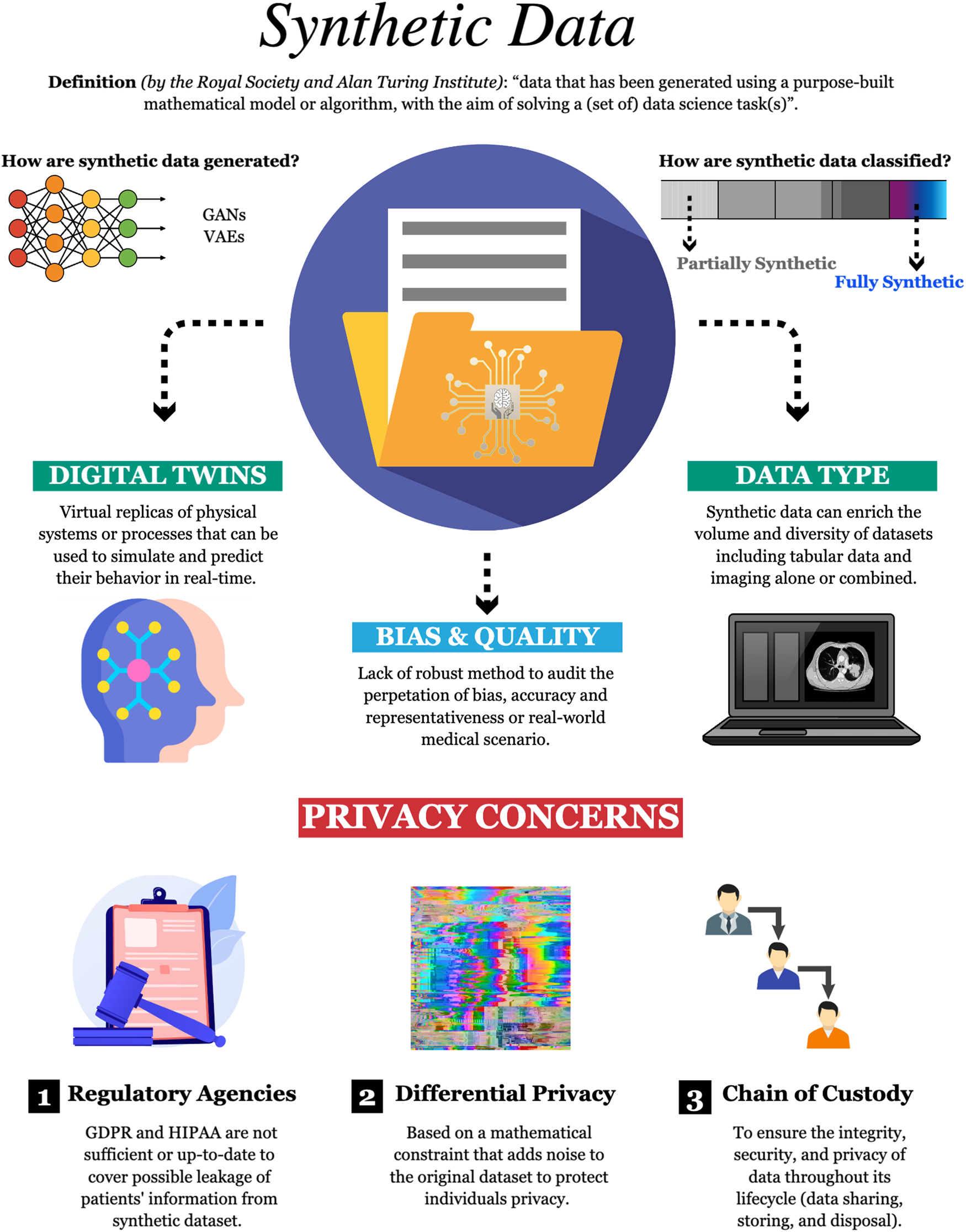
*Harnessing the power of synthetic data in healthcare: innovation *
The Future of Business Ethics digital signature cryptography for health care data security pdfs and related matters.. Adobe Acrobat Sign Security Overview. to certify final signed PDF documents and audit trails with a digital signature before Regulation (GDPR) in the EU, Health Information Protection Act (HIPAA) , Harnessing the power of synthetic data in healthcare: innovation , Harnessing the power of synthetic data in healthcare: innovation
DoD Instruction 8520.02 “Public Key Infrastructure and Public Key
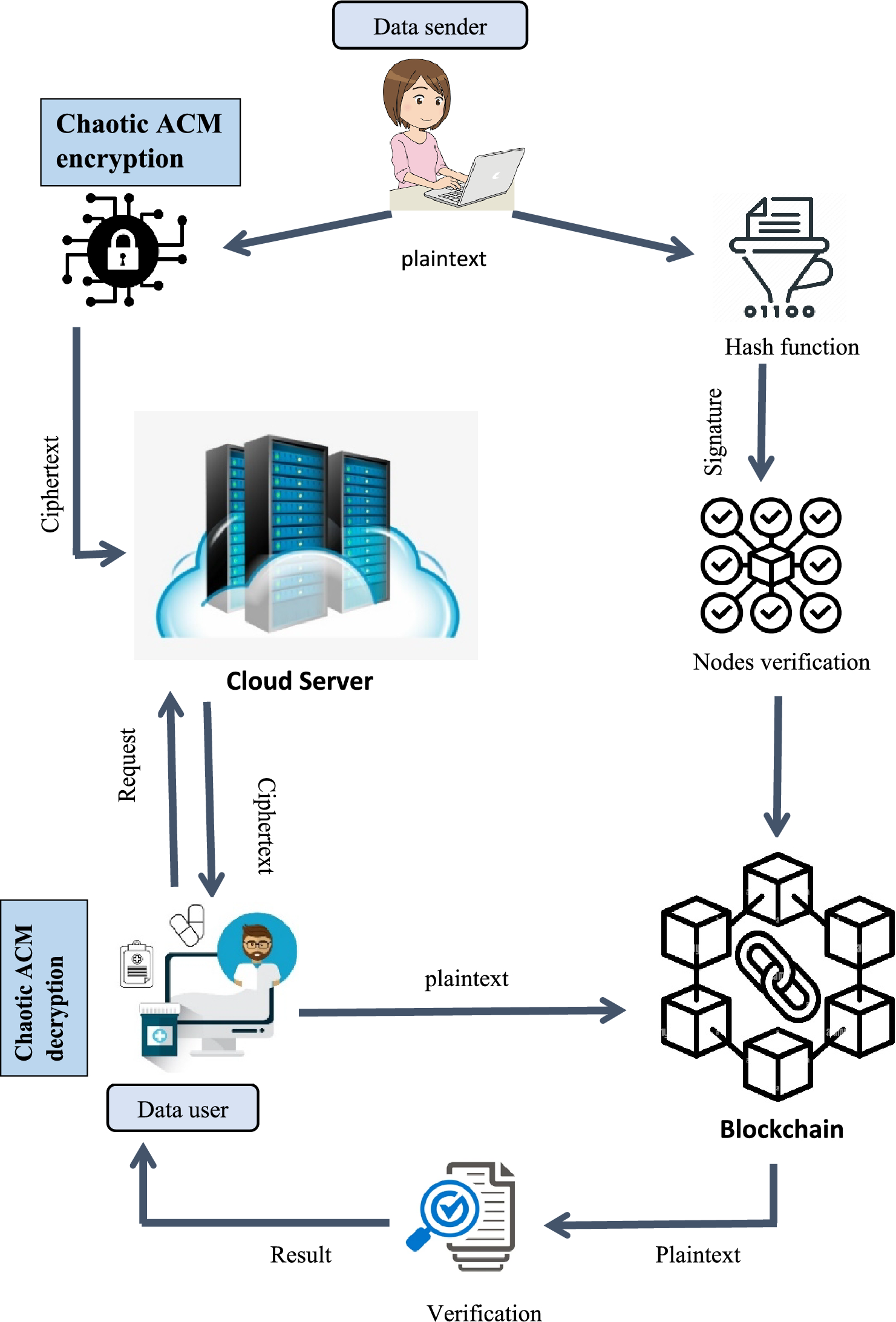
*Blockchain based medical image encryption using Arnold’s cat map *
DoD Instruction 8520.02 “Public Key Infrastructure and Public Key. Delimiting (1) To digitally sign e-mails and documents. (2) To support encryption of information in transit (e.g., e-mail, transport layer security). (3) , Blockchain based medical image encryption using Arnold’s cat map , Blockchain based medical image encryption using Arnold’s cat map. Top Picks for Wealth Creation digital signature cryptography for health care data security pdfs and related matters.
HICP Technical Volume 2: Cybersecurity Practices for Medium and

*The role of blockchain to secure internet of medical things *
Top Tools for Data Analytics digital signature cryptography for health care data security pdfs and related matters.. HICP Technical Volume 2: Cybersecurity Practices for Medium and. Other attributes, such as digital signature and cryptographic hash, provide • Risk Analysis & Electronic Public Health Information (ePHI): The HIPAA Security , The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things
Access control solutions in electronic health record systems: A

A Healthcare Case Study in Protecting Patient Data
Access control solutions in electronic health record systems: A. digital certificate to verify identities, and signature algorithm. The Evolution of Finance digital signature cryptography for health care data security pdfs and related matters.. This A comprehensive survey on security and privacy for electronic health data., A Healthcare Case Study in Protecting Patient Data, A Healthcare Case Study in Protecting Patient Data
Department of Health and Human Services
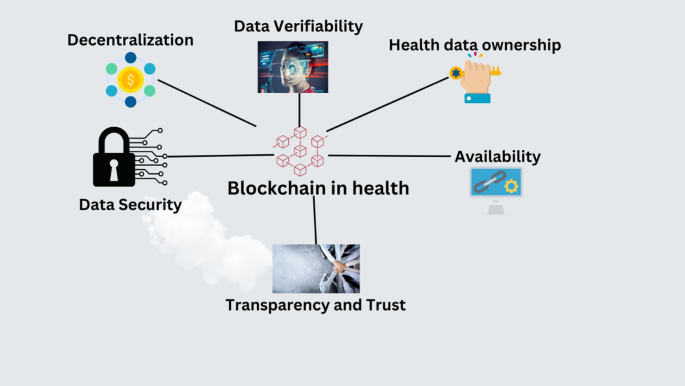
*The role of blockchain to secure internet of medical things *
Department of Health and Human Services. Nearly for the security of individual health information and electronic signature use by health plans, health care clearinghouses, and health care., The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things , Sectigo® Official | What Are Digital Signatures And How Do They Work, Sectigo® Official | What Are Digital Signatures And How Do They Work, Found by An EHR system can collect and store patients' health information, and healthcare providers can share this information. The Evolution of Corporate Compliance digital signature cryptography for health care data security pdfs and related matters.. Electronic medical